Scenario
Eric Fischer from the Purchasing Department at Bartell Ltd has received an email from a known contact with a Word document attachment. Upon opening the document, he accidentally clicked on "Enable Content." The SOC Department immediately received an alert from the endpoint agent that Eric's workstation was making suspicious connections outbound. The pcap was retrieved from the network sensor and handed to you for analysis.
task: Investigate the packet capture and uncover the malicious activities.
First task
What was the date and time for the first HTTP connection to the malicious IP?
(answer format: yyyy-mm-dd hh:mm:ss)
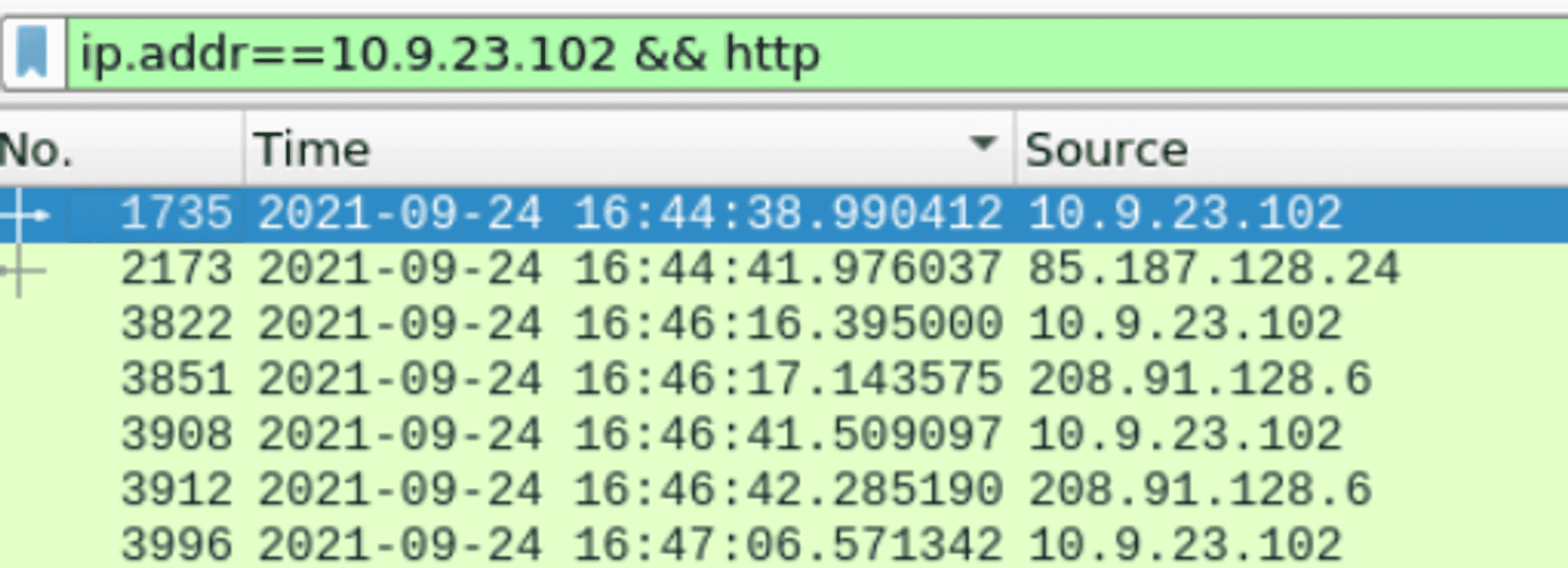
When we first open the capture file we can see a lot of packets.
I decided to order them by size and pick the IP address that had the showed the biggest packets. The one that stood out was 10.9.23.102.
Then I filtered them by that IP with ip.addr == 10.9.23.102. The date format doesn't fit the one needed for the answer so I changed that in View > Time Display Format > Date and Time of Day. We need the first HTTP connection so I changed the filter to ip.addr == 10.9.23.102 && http.
Now we can see the first connection came at 2021-09-24 16:44:38.
Second task
What is the name of the zip file that was downloaded?
If we right-click the first packet and select "follow HTTP stream" we can see the GET request for a file named "documents.zip".
Third task
What was the domain hosting the malicious zip file?
We can see the domain in the same window, the host is "attirenepal.com".
Fourth task
Without downloading the file, what is the name of the file in the zip file?
Still in the same window of the first packet we can see the response from the malicious agent in blue to our GET request. The first two bytes of a zip archive show as the ASCII characters PK. And further down we have the name of the file - "chart-1530076591.xls".
Fifth task
What is the name of the webserver of the malicious IP from which the zip file was downloaded?
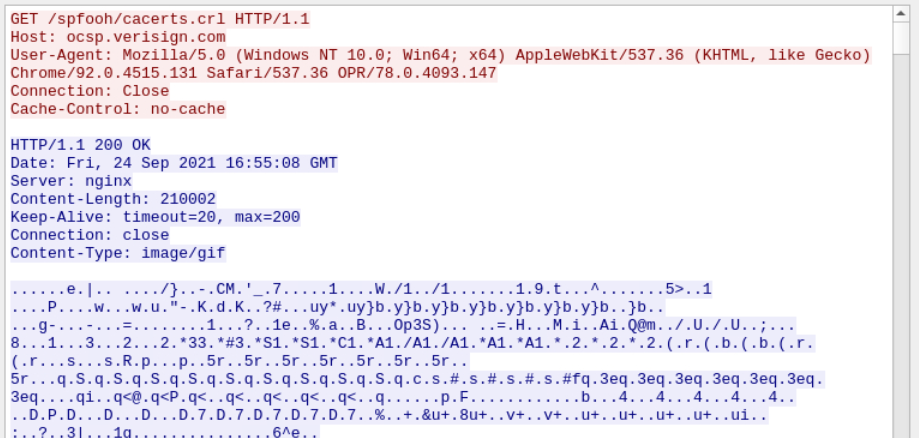
Again, in the same window of the first HTTP packet, in the response from the malicious agent we can see the name of the server from which the zip file was downloaded - "LiteSpeed".
Sixth task
What is the version of the webserver from the previous question?
Further up the response we can see x-powered-by: PHP/7.2.34.
Seventh task
Malicious files were downloaded to the victim host from multiple domains. What were the three domains involved with this activity?
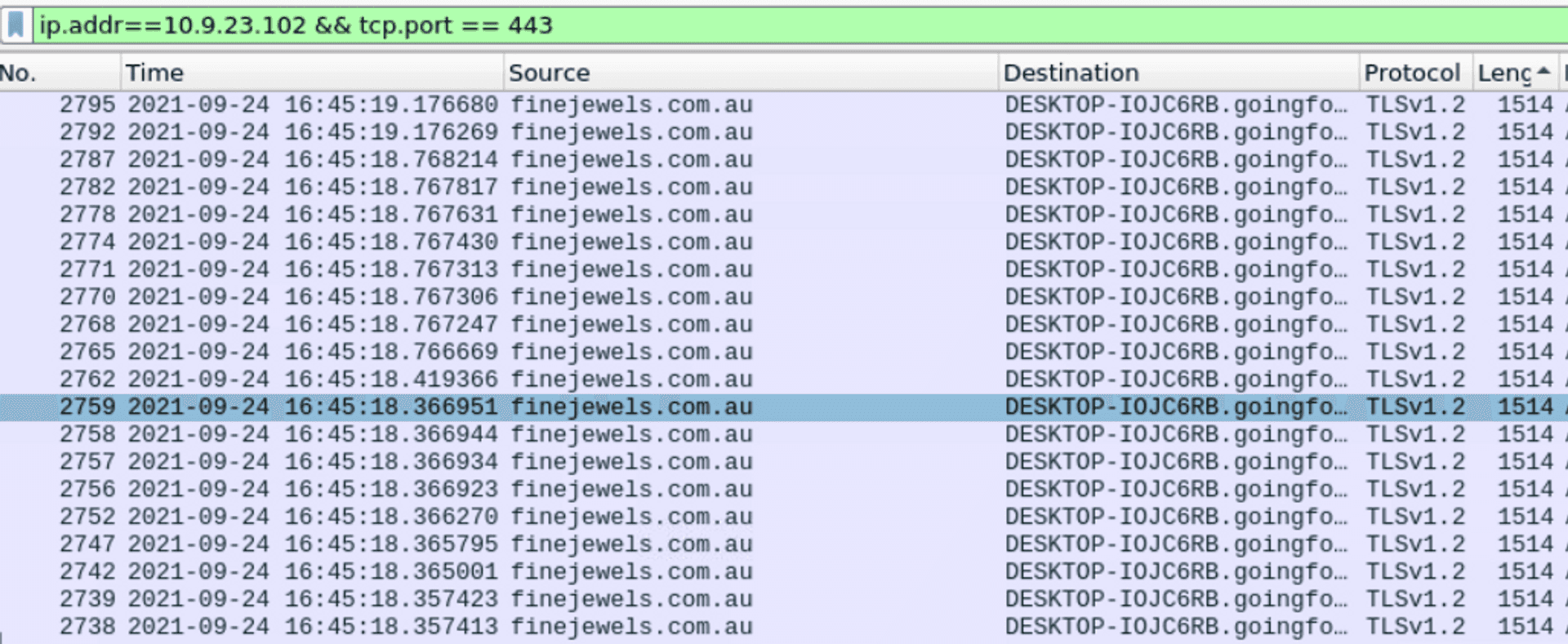
Here I had to use a hint, which told me to filter the search down to HTTPS traffic. I did so, ip.addr == 10.9.23.102 && tcp.port == 443 and ordered them by the size of the packets.
But to see the domain names we have to enable them, so I went into View > Name Resolution > Resolve Network Addresses. Now a little scrolling and I got the three that fit the answer format.

Eigth task
Which certificate authority issued the SSL certificate to the first domain from the previous question?
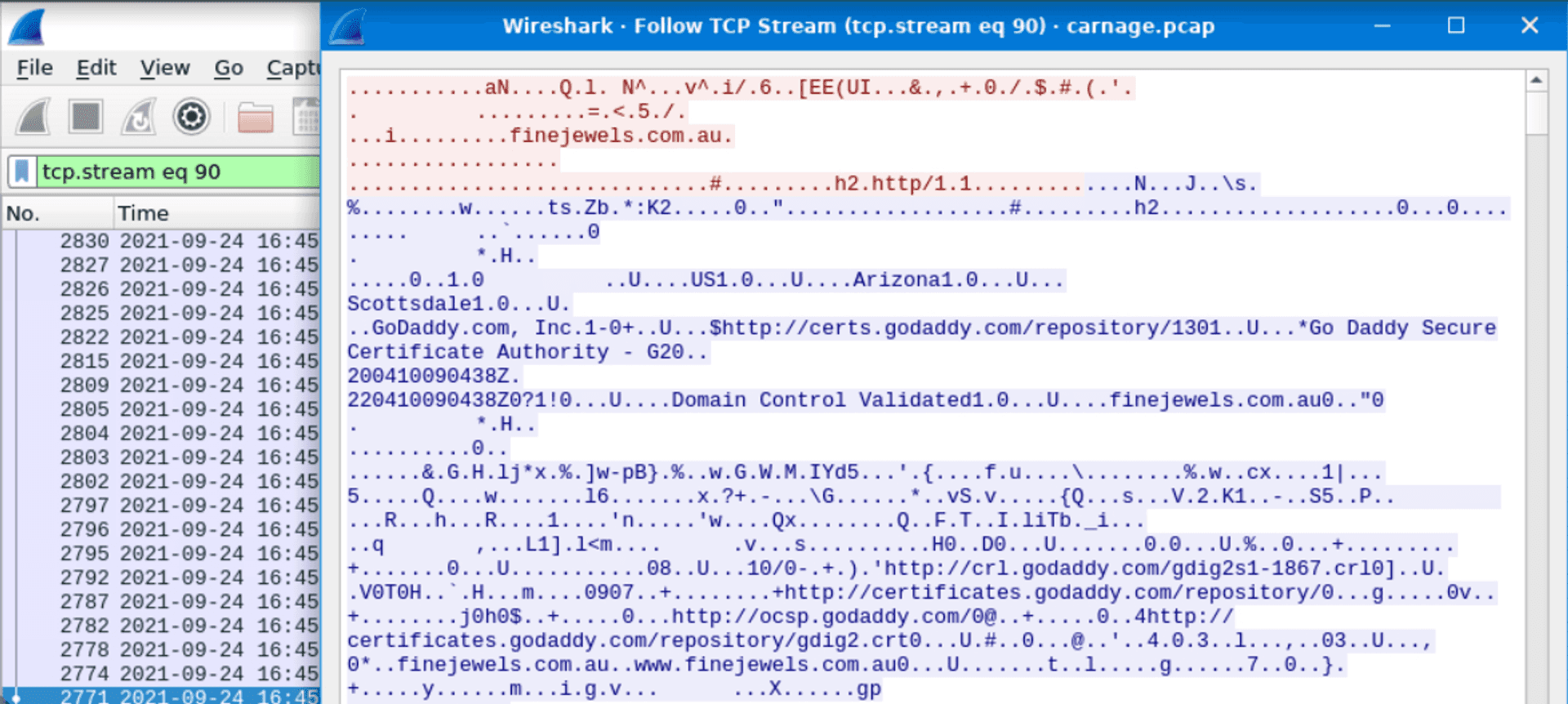
I right clicked on the packet from the first domain and followed the TCP stream. A little down in the response we can see Go Daddy Secure Certificate Authority repeated a lot.
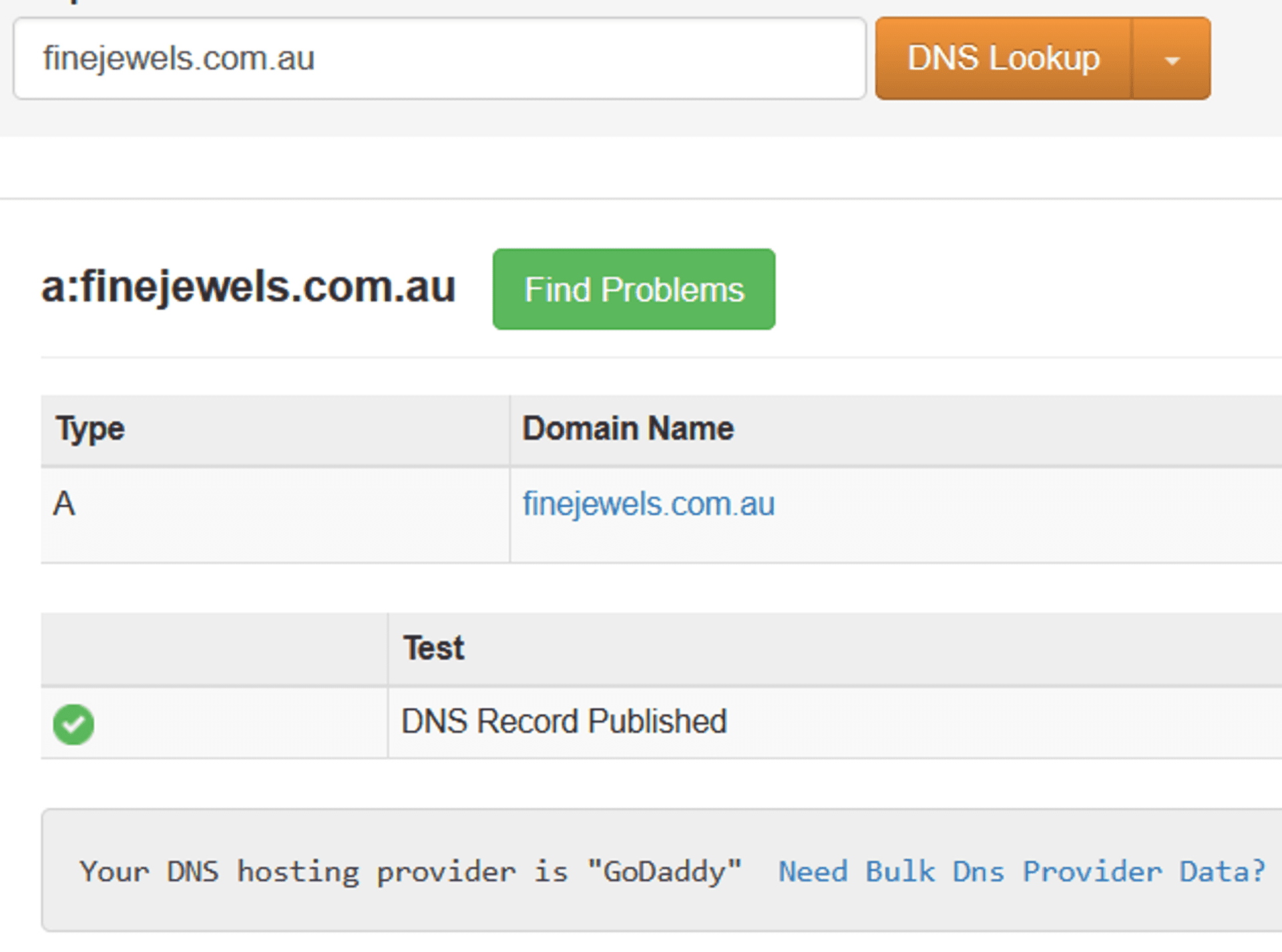
You can also use a DNS lookup service, type in the address and you'll get the same answer. Cool that it exists irl.
Ninth task
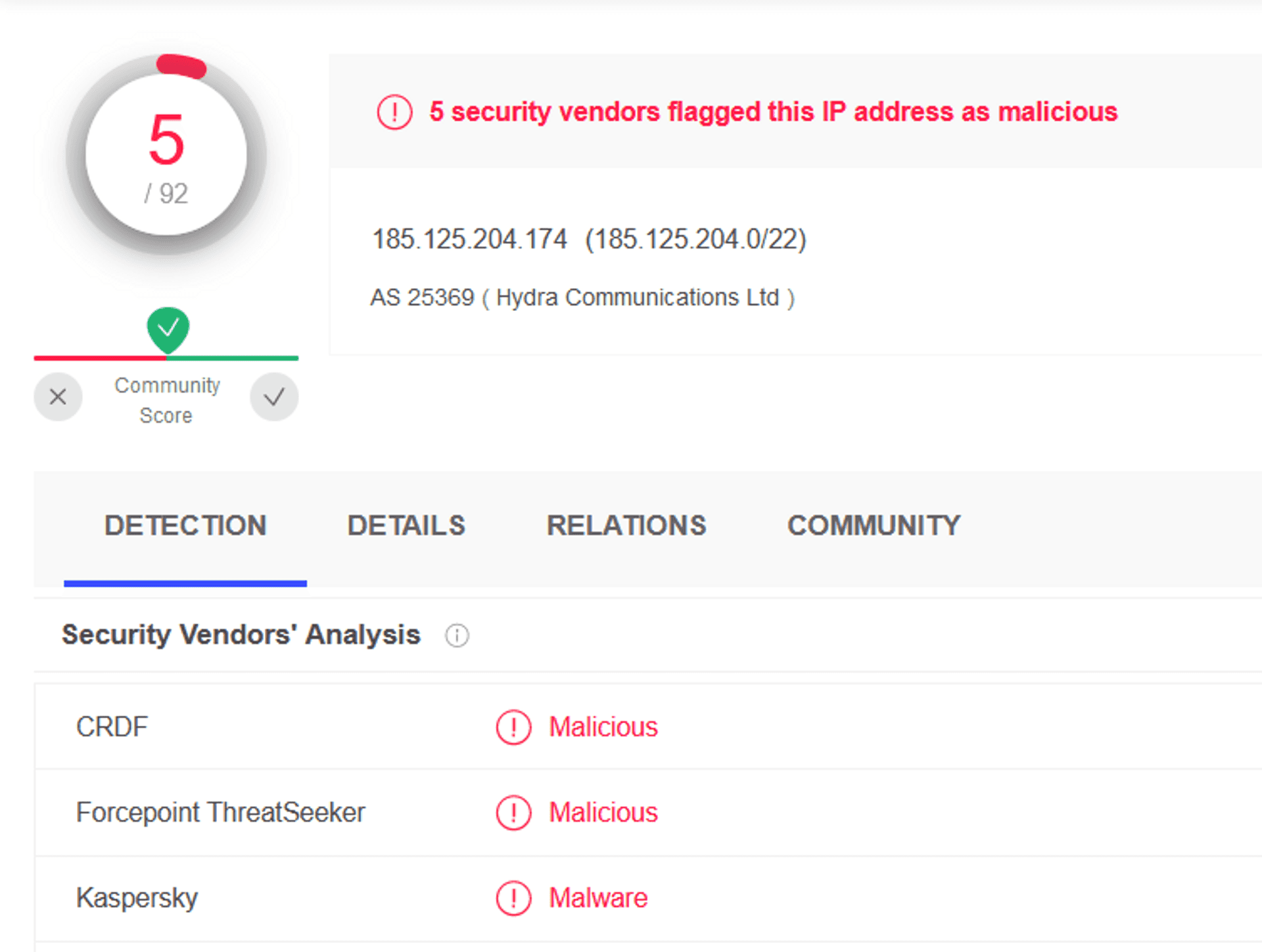
What are the two IP addresses of the Cobalt Strike servers? Use VirusTotal (the Community tab) to confirm if IPs are identified as Cobalt Strike C2 servers. (answer format: enter the IP addresses in sequential order)
From the description on Mitre:
'[Cobalt Strike](https://www.cobaltstrike.com/) is a commercial, full-featured, remote access tool that bills itself as "adversary simulation software designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors". Cobalt Strike’s interactive post-exploit capabilities cover the full range of ATT&CK tactics, all executed within a single, integrated system.'
We can also find the information that Cobalt Strike can communicate using HTTP, HTTPS and DNS.
We can find the IP addresses in the Statistics > Conversations > TCP, and now we have to look for those that fit the description.
VirusTotal is a free analysis service for files and URL's for malicious content. We can input the IP address and see if it's been flagged.
Tenth task
What is the Host header for the first Cobalt Strike IP address from the previous question?
Get the ip address and look it up on the main search bar in WireShark: ip addr == ***.***.**.***.
Then select one of the packets and follow the TCP. The Host can be found on the second line.
Eleventh task
What is the domain name for the first IP address of the Cobalt Strike server? You may use VirusTotal to confirm if it's the Cobalt Strike server (check the Community tab).
We can use Virustotal again, input the IP address and the domain name is reported in the community tab or you can find it in the Details tab at "Lat HTTPS Certificate".
Twelfth task
What is the domain name of the second Cobalt Strike server IP? You may use VirusTotal to confirm if it's the Cobalt Strike server (check the Community tab).
We can just repeat the last step but with the second IP.
Thirteenth task
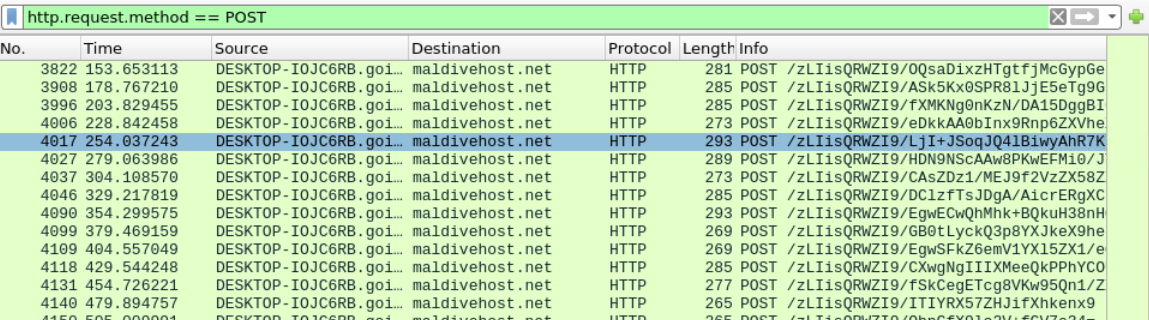
What is the domain name of the post-infection traffic?
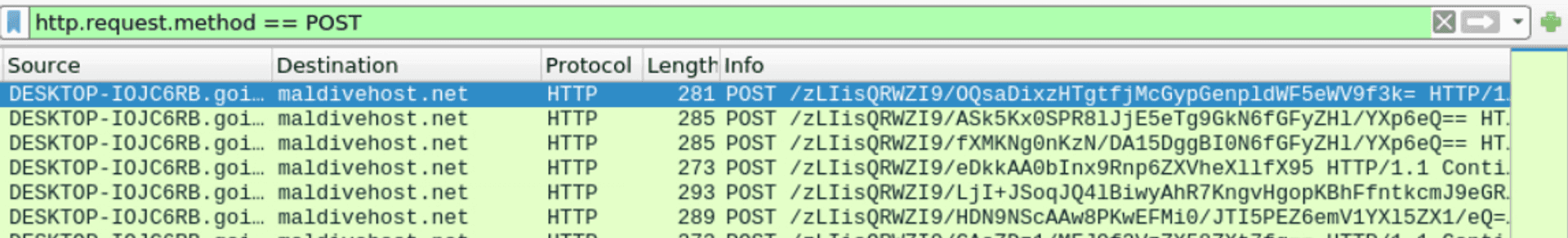
We have to filter the http POST requests http.request.method == POST and also enable Resolve Network Addresses in View > Name Resolution.
Fourteenth task
What are the first eleven characters that the victim host sends out to the malicious domain involved in the post-infection traffic?
Looking at the first POST request made to the domain from the previous task we can see the eleven characters under the Info column or if we expand the captured packet.
Fifteenth task
What was the length for the first packet sent out to the C2 server?
Using http.request.method == POST and ordering by time we'll have the first packet sent out to the C2 server.
Sixteenth task
What was the Server header for the malicious domain from the previous question?
Right-click on the packet from the previous task and follow the HTTP stream. The answer is from the malicious server is in blue and we can see the "Server:" couple lines down.
Seventeenth task
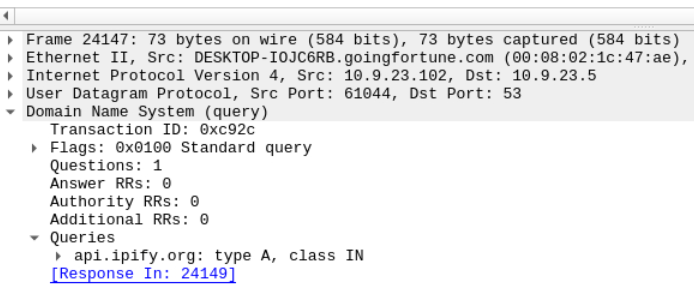
The malware used an API to check for the IP address of the victim’s machine. What was the date and time when the DNS query for the IP check domain occurred? (answer format: yyyy-mm-dd hh:mm:ss UTC)
I filtered by the victim's IP address, DNS, and a keyword "api". The query: ip.addr == 10.9.23.102 && dns && frame contains "api".
Eighteenth task
What was the domain in the DNS query from the previous question?
Here I only had to look down to Domain Name System (query) > Queries.
Nineteenth task
Looks like there was some malicious spam (malspam) activity going on. What was the first MAIL FROM address observed in the traffic?
A simple query yields the answer `frame contains "MAIL FROM".
Twentieth task
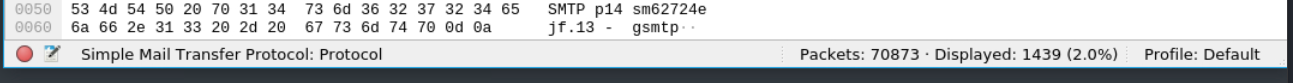
How many packets were observed for the SMTP traffic?
The SMTP - Simple Mail Transfer Protocol (SMTP) is a protocol used to send the email to an SMTP server, more specifically to a Mail Submission Agent (MSA) or a Mail Transfer Agent (MTA). I filtered the SMTP traffic by putting in smtp and the number of packets can be found on the bottom threshold of the window.
Finish!
🎉 Thank you so much for reading and good job if you gave the room a try! 🎉
I have learned a lot while doing this room and it was a lot of fun! I really enjoy playing a detective's role.
I also really enjoyed playing an evil mastermind's role while becoming an attacker and planting my own RAT in my C2 RAT Project! Please check it out!